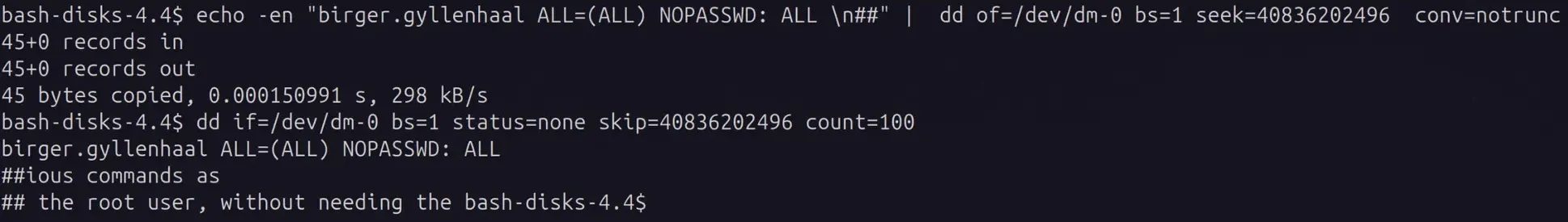
Linux Arbitrary File Write and Privilege Escalation with dd
The disk group seems innocent enough - it’s meant for disk management utilities. But give someone disk group access and you’ve essentially handed them root. Here’s how to exploit raw block device access to bypass all file permissions and escalate privileges. While the XKCD comic above is tongue-in-cheek, using dd for filesystem manipulation is genuinely powerful and dangerous. The Linux disk group allows raw access to disks on the system. It’s meant to allow members to use tools to manage disk partitions and format disks at the block level. However, it can also be used to get arbitrary file read/write by directly editing the disk contents even if file system permissions forbid it. For this reason it is a very privileged group and should be considered equivalent to root access. ...
Cloudflare WARP Config Generator
A browser-based and CLI tool for generating WireGuard configurations compatible with Cloudflare WARP. The application generates keypairs locally in the browser or CLI, registers them with Cloudflare’s WARP API, and outputs a complete WireGuard configuration file with QR code for easy mobile import. All processing happens client-side with no server-side storage. Configuration options include DNS server selection, MTU adjustment, allowed IPs, and persistent keepalive settings. A command-line shell script is also available for terminal-based workflows. ...
MikroTik SwOS Python Library
Got a bunch of MikroTik switches running SwOS or SwOS Lite with no good way to manage them centrally? This library has you covered. Built by reverse engineering the SwOS HTTP API, it provides complete programmatic access to all switch features. Works with both SwOS and SwOS Lite, supports everything from port configs and PoE to VLANs and SNMP settings. Comes with a CLI tool for quick lookups and a full Ansible module for managing your entire switch fleet through YAML playbooks. Compatible with CRS305, CRS310, CRS326, CSS610 and other SwOS-based switches.
TRMNL Plugins
A collection of custom plugins for TRMNL e-ink displays. The repository provides a Docker-based development environment for creating and testing plugins that extend TRMNL functionality.

Software Supply Chain Security: The Case for Minimal Dependencies
In 2016, removing an 11-line npm package called left-pad broke thousands of projects worldwide. Nine years later, attackers compromised packages with 2.6 billion weekly downloads using phishing and self-propagating malware. The Problem: A Decade of Escalating Supply Chain Attacks Timeline March 2016: Left-pad incident - removing an 11-line dependency broke thousands of projects including Babel and React. October 2021: ua-parser-js compromise - library with 7M+ weekly downloads hijacked multiple times, injecting cryptocurrency miners and password stealers. ...
Drouter
Drouter provides dynamic route injection for Docker containers through label-based configuration. The systemd service monitors Docker containers and automatically configures static routes in their network namespaces without requiring elevated privileges within the containers themselves. The system uses Docker labels to specify routing rules and applies them automatically when containers start or stop. This enables complex networking setups where containers need custom routing tables while maintaining security by avoiding privileged container execution for network configuration tasks.
Drouter: Dynamic Route Injection for Docker Containers
When working with Docker containers on complex networks, you often need to add static routes so containers can reach networks that aren’t directly connected to their default gateway. This becomes especially important when using macvlan network drivers where containers get their own IP addresses on your physical network. I’ve just released drouter, a lightweight systemd service that solves this problem by automatically injecting routes into Docker containers based on simple labels. The Problem Consider this scenario: you’re using a macvlan network driver so your containers get real IP addresses on your network (say 192.168.1.0/24). Your router is at 192.168.1.1, but you have additional internal subnets like 10.0.0.0/8 that are reachable through a different gateway at 192.168.1.254. ...
ARIN IPv4 Waitlist Tracking
ARIN IPv4 Wait-list Tracking analyzes ARIN’s IPv4 address wait-list and provides statistical insights into wait times and allocation patterns. The Python-based system tracks historical data on IPv4 block requests and clearances to estimate processing times for different network block sizes. The web dashboard displays real-time analytics including current wait-list sizes, estimated wait times for /22, /23, and /24 blocks, and historical trends in IPv4 address allocation. This tool helps network administrators understand IPv4 scarcity patterns and plan address allocation strategies as IPv4 exhaustion continues.
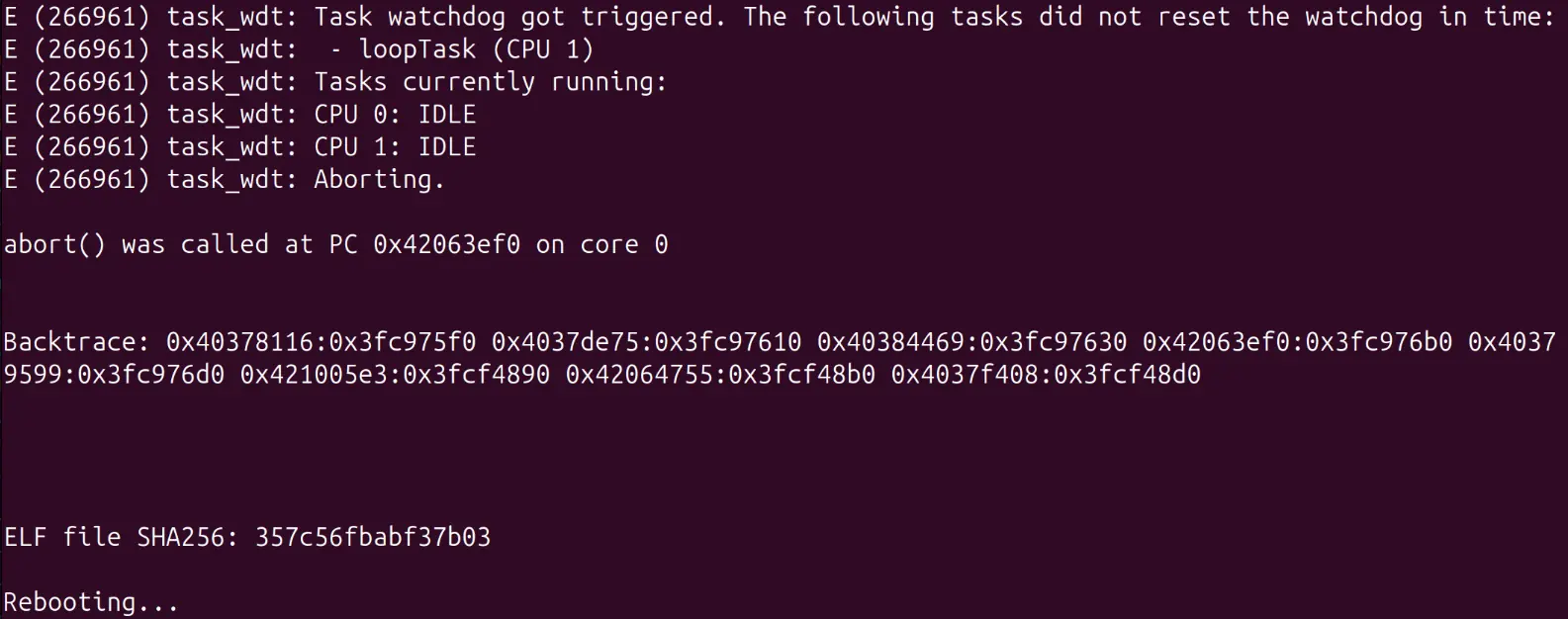
ESPHome ESP32 Coredump Debugging
When developing with ESPHome on ESP32 devices, crashes can be frustrating to debug without proper stack traces. Enabling coredumps provides detailed crash information to help identify the root cause of issues. Configuration To enable coredump functionality, you’ll need to modify your ESPHome configuration and create a custom partition table. This setup is for the Arduino framework - ESP-IDF configurations will differ slightly. ESPHome Configuration Add the following to your ESPHome YAML configuration: ...
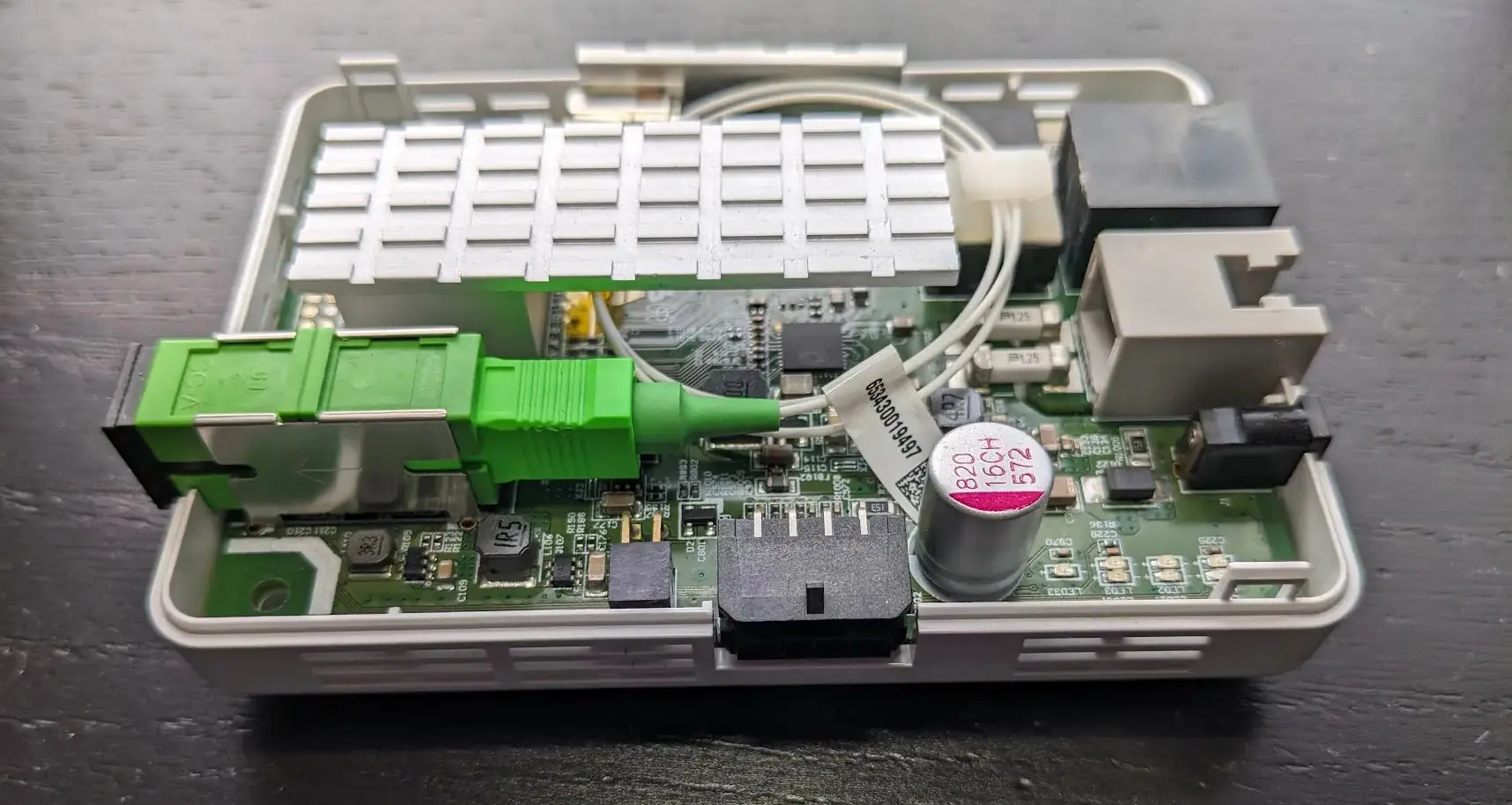
Adtran Fiber ISP Hacking
Adtran 411 Security Audit Adtran produces equipment for fiber ISPs. I was provided an Adtran 411 by my current ISP for Internet access and decided to take a deep look into it. Hardware The Adtran 411 is a small GPON fiber ONT (Optical Network Terminal) designed to give symmetrical gigabit fiber Internet to SOHO users. It connects to the ISP via a GPON uplink and provides the user a normal ethernet RJ-45 connector to plug their router into and a RJ-11 port for a landline to be tunneled over VOIP. ...