Recently there has been a lot of buzz about the recent Heartbleed vulnerability found in some versions of OpenSSL. The attack works due to a mistake in the server validating part of the request made by the SSL client. The popular web comic XKCD has made a great simple comic explaining how the attack works, and there are simple tools to test for vulnerable servers.
But how does this affect me, a user?
Well, if any of the services you used were vulnerable, you should at least change your password. Ideally the administrators of the service are aware of this attack and have fixed the issue on their end, and hopefully revoked their previous SSL certificate and issued a new one. If they have not, then you should really consider moving your data elsewhere.
For the web, most web browsers will automatically check for revoked certificates and warn the user if they try to visit a site that is using a certificate that has been revoked. However, Google Chrome, currently the most popular web browser, does not check if a server’s certificate has been revoked by default. Safari, Firefox, and even Internet Explorer do perform this check by default. But don’t worry, CRL (certificate revocation list) checking can be enabled!
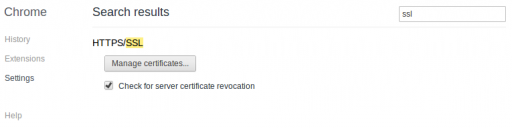
To enable CRL checking in Chrome enter chrome://settings into the address bar and press enter. Once on the settings page, enter “ssl” into the search box. Finally check the box next to “Check for server certificate revocation”. That’s all!
To verify that certificate revocation checking works, you can visit https://www.cloudflarechallenge.com. If the page loads then your browser is not checking for revoked certs. If you see an error, then your browser noticed that the certificate being used on the server has been revoked and is doing its job.
More information about how the Heartbleed attack affects certificates can be found here.
UPDATE: Enabling CRL checking is good, but it is not a full solution. CRL does not work on large scales, to learn more read this.