This is a simple how-to on using Microsoft’s Active Directory for user authentication on Linux systems. The method described in this guide should work for Cent OS, Red Hat Enterprise Linux (RHEL), and Fedora. Debian based distributions do not the the tools used in this method and require a different setup. This guide used Cent OS 5.5 with a minimal text only install, however it should apply the same to other compatible versions of Linux.
Installing the Software
We will need two packages installed to join the Active Directory (AD) domain and use it for user authentication, authconfig and samba-common. authconfig should be installed by default but with a minimal install you will need to install samba. Install them with the following command:
yum install samba-common authconfig
Setting up Authconfig
Start authconfig by running authconfig-tui, if you have a graphical desktop such as gnome installed you can launch it from System->Administration->Authentication but this guide will cover the text/cli version. But the same steps apply to both methods.
- Under user information select “Use Windbind”
- Under authentication select “Use MD5 Passwords”, “Use Shadow Passwords”, “Use Windbind Authentication”, and “Local authorization is Sufficient”.
- Your screen should look like this:
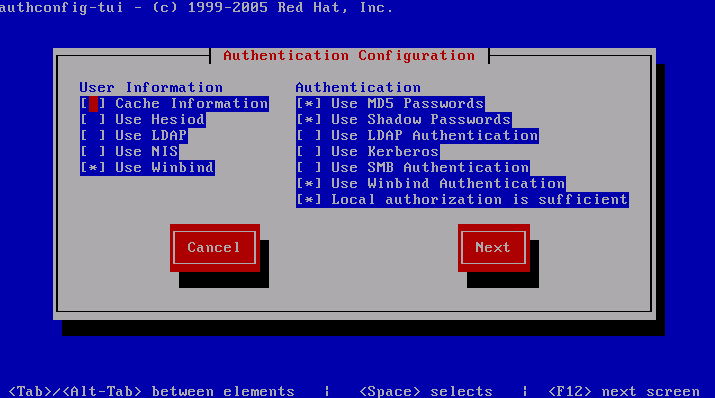
- Click Next
- Change the “Security Model” to “domain”
- Under “Domain” enter your active directory domain.
- Enter the FQDN (fully-qualified domain name) of your domain servers, if you have more than one you can separate them with a comma.
- The ADS realm is the full domain, it must be in call caps.
- To allow users to login change the template shell to /bin/bash, or whatever shell you prefer.
- The screen should now look like this, but with your correct information:
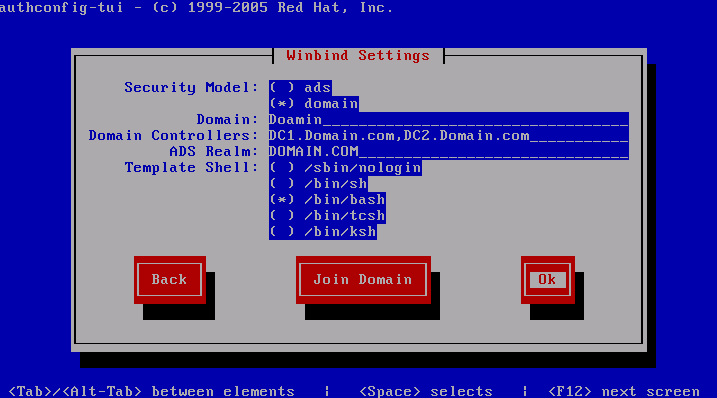
- Select OK.
Setting Up Samba
Now you need to edit /etc/samba/smb.conf. You will see many of the settings you just entered in this file, however we still need to manually change one value that authconfig does not do for us. Look for “windbind use default domain” and change it from false to true.
Setting up PAM
PAM controls user logins. and we need to create a home directory for domain users on their first login. All domain users will have a home directory in /home/Domain/user, where Domain is your domain and user is their username. Create the Domain folder inside the /home directory with the mkdir command as root.
Next we need to enable the user’s home directory creation in PAM. Edit /etc/pam.d/system-auth. Scroll to the end of the file and at the end add this:
session optional pam_mkhomedir.so
Save the file and exit. To make these changes take effect we need to restart the windbind service and the oddjobd service. This can usually be done with the service command. I will not cover that here.
Joining the Domain
Now that the system is configured correctly we will actually join the system to the Active Directory domain. run the “authconfig-tui” program again. Click next. And this time on the second screen select “Join Domain”. Enter a domain administrator’s username and password and join the domain. After entering the credentials select OK to save and exit.
You are now done, you should be able to log out (as root) and log in as any domain member. Upon first login your come directory should be created automatically.
